The Cost of a Data Breach: 50 Key Statistics and Insights
Data breaches have become a pervasive threat in our digital age, with organizations across the globe facing increasing risks. The consequences of a data breach extend far beyond the immediate security concerns; they can result in substantial financial losses, damage to reputation, and legal consequences. In this comprehensive blog, we'll
Read moreWhat is a proof of concept (POC)?
In a world driven by innovation and technology, the process of developing new ideas, products, and solutions is often a complex and uncertain journey. This is where a Proof of Concept (POC) comes into play. In this extensive guide, we will delve into the concept of POCs, their significance, the
Read moreEnhancing Blockchain Security With Cryptography
Blockchain technology has revolutionized the way we think about data storage, security, and trust. However, like any technological advancement, it is not immune to security threats. This is where cryptography comes to the rescue. In this comprehensive guide, we will explore how cryptography plays a pivotal role in enhancing blockchain
Read moreHow to Conduct a Secure Code Review
Cyber threats continue to evolve, making it essential for organizations to employ comprehensive security measures. Secure code reviews are a crucial aspect of this strategy. In this in-depth guide, we'll explore how to conduct a secure code review effectively, emphasizing the importance of safeguarding your software against vulnerabilities and cyberattacks.
Read moreWhat Are Improper Error Handling Vulnerabilities?
Software developers and security professionals face the daunting challenge of protecting systems and applications from a myriad of threats. One often-overlooked aspect of cybersecurity is improper error handling vulnerabilities. In this comprehensive guide, we'll dive into what improper error handling vulnerabilities are, the risks they pose, and effective solutions to
Read moreFix the Windows Security App When It’s Not Starting or Crashing
Windows Security, previously known as Windows Defender, is a crucial component of your Windows operating system, designed to protect your PC from malware, viruses, and other security threats. However, sometimes users encounter issues with Windows Security, such as it not starting or crashing. In this guide, we will walk you
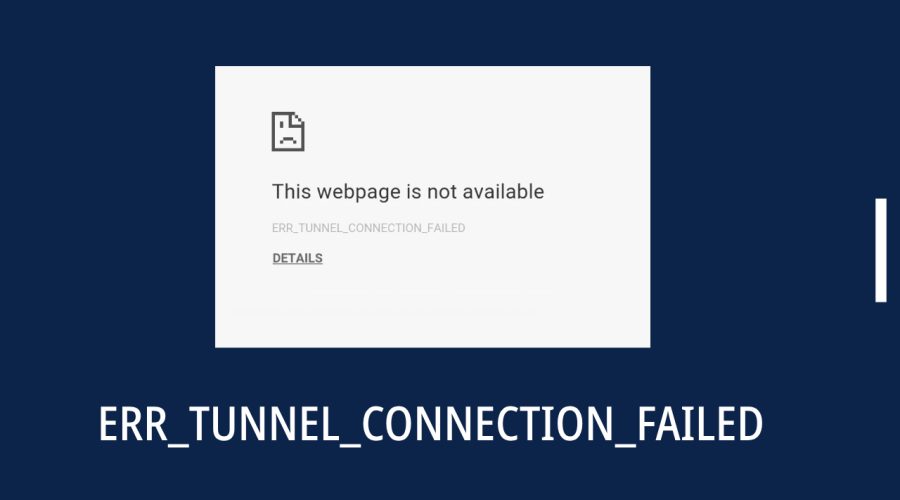
Read moreHow to Fix ERR_TUNNEL_CONNECTION_FAILED in Google Chrome
Google Chrome is a popular web browser known for its speed and reliability, but like any software, it's not immune to errors. One common error that Chrome users may encounter is "ERR_TUNNEL_CONNECTION_FAILED." This error can be frustrating, as it prevents you from accessing websites. However, it's essential to address it
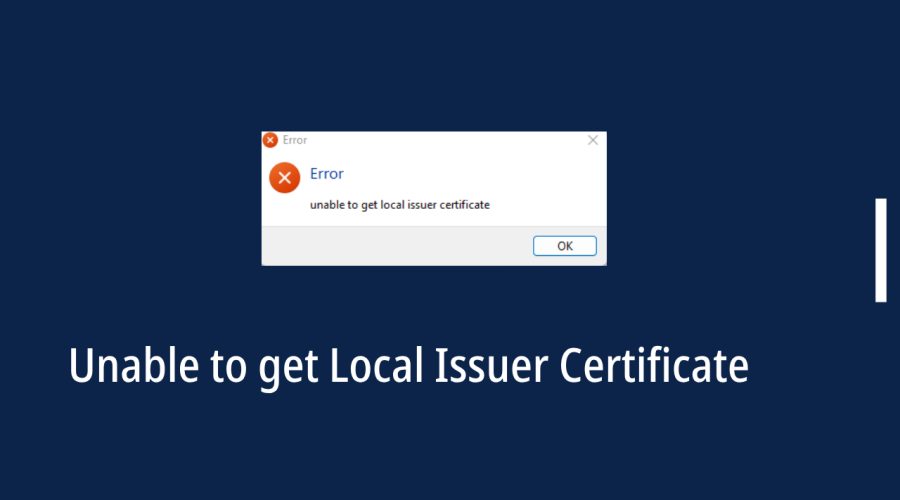
Read moreHow to Fix the SSL Certificate Problem: Unable to Get Local Issuer Certificate
SSL certificates play a crucial role in ensuring the safety of data transmitted over the internet. However, encountering SSL certificate problems is not uncommon. One such issue is the "SSL Certificate Problem: Unable to Get Local Issuer Certificate." This error can be frustrating, but it's essential to address it promptly
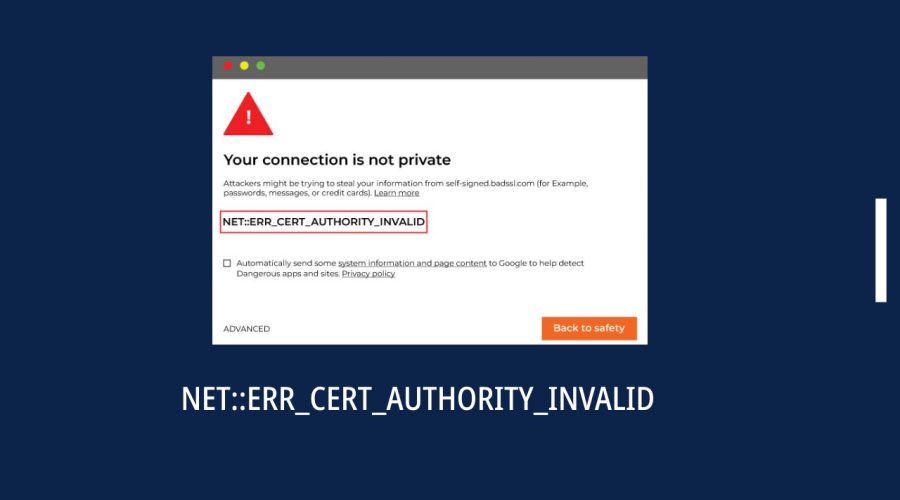
Read moreHow to Fix NET::ERR_CERT_AUTHORITY_INVALID Error on Chrome?
The "NET::ERR_CERT_AUTHORITY_INVALID" error is a common SSL/TLS-related error in Google Chrome. It occurs when Chrome detects an issue with a website's SSL certificate, typically due to problems with the certificate's authority or chain of trust. In this guide, we'll walk you through the steps to resolve this error and safely
Read more